Palo Alto Networks’ Unit 42 threat intelligence team published a report about Docker images that contain Cryptojacking malware distributed via Docker Hub.
Palo Alto Networks’ Unit 42 threat intelligence team said that the purpose of these Docker images is to make money by deploying a cryptocurrency miner using Docker containers and leveraging the Docker Hub repository to distribute these images.
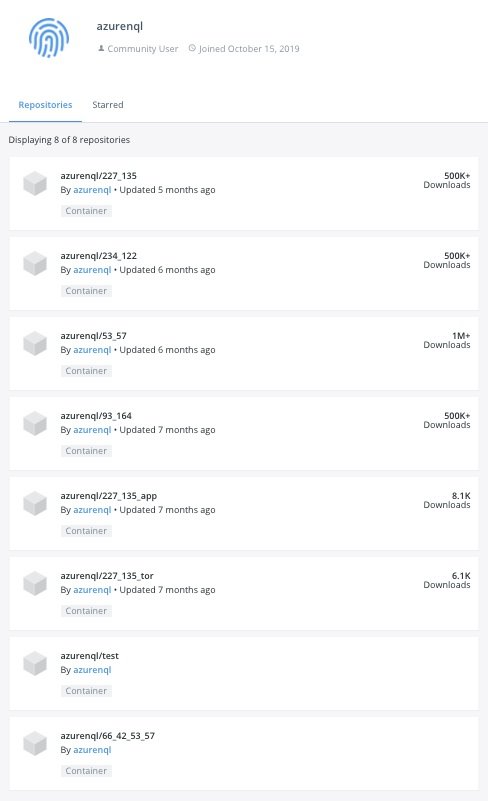
Six malicious images hosted on a Docker Hub account
A malicious Docker Hub account, azurenql, active since October 2019 has been identified by Palo Alto Networks’ Unit 42 threat intelligence team. This Docker Hub account was hosting six malicious images intended to mine the cryptocurrency, Monero. The attacker used a Python script to trigger the cryptojacking operation and took advantage of network anonymizing tools such as ProxyChains and Tor to evade network detection. The top image was pulled more than 1.47 million times.
Docker servers are also in danger
Meanwhile, Trend Micro researchers also found that unprotected Docker servers are being targeted with at least two different kinds of malware named XOR DDoS and Kaiji to collect system information and carry out DDoS attacks.
According to Trend Micro researchers, attackers usually used botnets to perform brute-force attacks after scanning for open Secure Shell (SSH) and Telnet ports. Now, they are also searching for Docker servers with exposed ports (2375).
They analyzed XOR DDoS and Kaiji malwares and shared details about them. They recommend for securing servers:
- Secure the container host. Take advantage of monitoring tools, and host containers in a container-focused OS.
- Secure the networking environment. Use the intrusion prevention system (IPS) and web filtering to provide visibility and observe internal and external traffic.
- Secure the management stack. Monitor and secure the container registry and lock down the Kubernetes installation.
- Secure the build pipeline. Implement a thorough and consistent access control scheme and install strong endpoint controls.
- Adhere to the recommended best practices.
- Use security tools to scan and secure containers.
